반응형
🔹 Anti-VM 우회 분석 오픈소스 al-khaser v0.81
Anti-VM 악성코드에서 사용하는 우회 방법을 역으로 활용하여 VM(Virtual Machine), Sandbox 환경인지 확인하는 프로그램입니다.
💡 - 현재 Chrome 세이프 브라우징 기능으로 exe(Binary) 파일은 제공하지 않음 - Visual Studio를 통해 exe build 작업 필요 - 2019년 이후로 업데이트가 되지 않음 (소스코드를 직접 수정, 빌드하여 상황에 맞는 사용하는 방법이 있음)
🔹 주요 기능
Anti-debugging attacks
- IsDebuggerPresent
- CheckRemoteDebuggerPresent
- Process Environment Block (BeingDebugged)
- Process Environment Block (NtGlobalFlag)
- ProcessHeap (Flags)
- ProcessHeap (ForceFlags)
- Low Fragmentation Heap (LFH)
- NtQueryInformationProcess (ProcessDebugPort)
- NtQueryInformationProcess (ProcessDebugFlags)
- NtQueryInformationProcess (ProcessDebugObject)
- WudfIsAnyDebuggerPresent
- WudfIsKernelDebuggerPresent
- WudfIsUserDebuggerPresent
- NtSetInformationThread (HideThreadFromDebugger)
- NtQueryObject (ObjectTypeInformation)
- NtQueryObject (ObjectAllTypesInformation)
- CloseHanlde (NtClose) Invalide Handle
- SetHandleInformation (Protected Handle)
- UnhandledExceptionFilter
- OutputDebugString (GetLastError())
- Hardware Breakpoints (SEH / GetThreadContext)
- Software Breakpoints (INT3 / 0xCC)
- Memory Breakpoints (PAGE_GUARD)
- Interrupt 0x2d
- Interrupt 1
- Trap Flag
- Parent Process (Explorer.exe)
- SeDebugPrivilege (Csrss.exe)
- NtYieldExecution / SwitchToThread
- TLS callbacks
- Process jobs
- Memory write watching
- Page exception breakpoint detection
- API hook detection (module bounds based)
Anti-injection
- Enumerate modules with EnumProcessModulesEx (32-bit, 64-bit, and all options)
- Enumerate modules with ToolHelp32
- Enumerate the process LDR structures with LdrEnumerateLoadedModules
- Enumerate the process LDR structures directly
- Walk memory with GetModuleInformation
- Walk memory for hidden modules
Anti-Dumping
- Erase PE header from memory
- SizeOfImage
Timing Attacks [Anti-Sandbox]
- RDTSC (with CPUID to force a VM Exit)
- RDTSC (Locky version with GetProcessHeap & CloseHandle)
- Sleep -> SleepEx -> NtDelayExecution
- Sleep (in a loop a small delay)
- Sleep and check if time was accelerated (GetTickCount)
- SetTimer (Standard Windows Timers)
- timeSetEvent (Multimedia Timers)
- WaitForSingleObject -> WaitForSingleObjectEx -> NtWaitForSingleObject
- WaitForMultipleObjects -> WaitForMultipleObjectsEx -> NtWaitForMultipleObjects (todo)
- IcmpSendEcho (CCleaner Malware)
- CreateWaitableTimer
- CreateTimerQueueTimer
- Big crypto loops (todo)
Human Interaction / Generic [Anti-Sandbox]
- Mouse movement
- File names like sample.exe or sandbox.exe.
- Total Physical memory (GlobalMemoryStatusEx)
- Disk size using DeviceIoControl (IOCTL_DISK_GET_LENGTH_INFO)
- Disk size using GetDiskFreeSpaceEx (TotalNumberOfBytes)
- Mouse (Single click / Double click) (todo)
- DialogBox (todo)
- Scrolling (todo)
- Execution after reboot (todo)
- Count of processors (Win32/Tinba - Win32/Dyre)
- Sandbox known product IDs (todo)
- Color of background pixel (todo)
- Keyboard layout (Win32/Banload) (todo)
- Genuine Windows installation.
- Known Sandbox hostnames and usernames
Anti-Virtualization / Full-System Emulation
- Registry key value artifacts
- Registry Keys artifacts
- File system artifacts
- Directories artifacts
- Memory artifacts
- MAC Address
- Virtual devices
- Hardware Device information
- System Firmware Tables
- Driver Services
- Adapter name
- Windows Class
- Network shares
- Processes
- WMI
- DLL Exports and Loaded DLLs
- CPU
- NtQueryLicenseValue with Kernel-VMDetection-Private as license value.
Anti-Analysis
- Processes
Anti-Disassembly
- Jump with constant condition
- Jump instruction with same target
- Impossible disassembly
- Function Pointers
- Return Pointer Abuse
Macro malware attacks
- Document_Close / Auto_Close.
- Application.RecentFiles.Count
Code/DLL Injections techniques
- CreateRemoteThread
- SetWindowsHooksEx
- NtCreateThreadEx
- RtlCreateUserThread
- APC (QueueUserAPC / NtQueueApcThread)
- RunPE (GetThreadContext / SetThreadContext)
🔹 악성코드 분석환경에서 실제 동작 스크린샷
테스트 환경 : VMware - Windows 10
동작 스크린샷 (Good / Bad)
아래 스크린샷과 같이 Good / Bad로 분석환경이 일반적인 알려진 Anti-VM 기법에서 우회 가능 유무를 확인할 수 있고, Bad 항목에 대해 적절한 조치로 Anti-VM 우회를 막을 수 있음
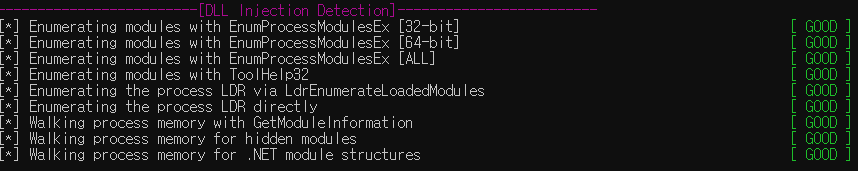



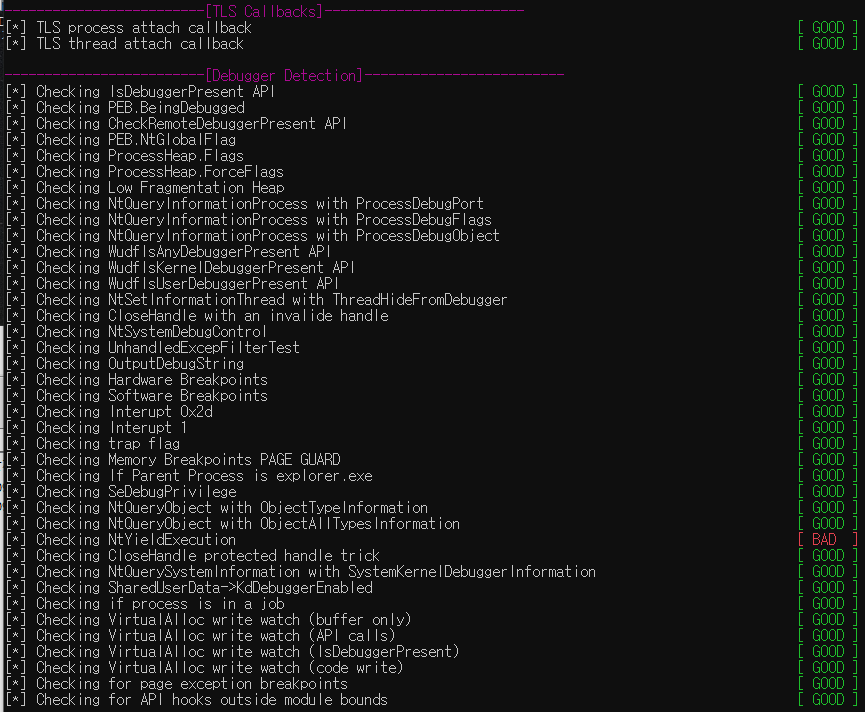
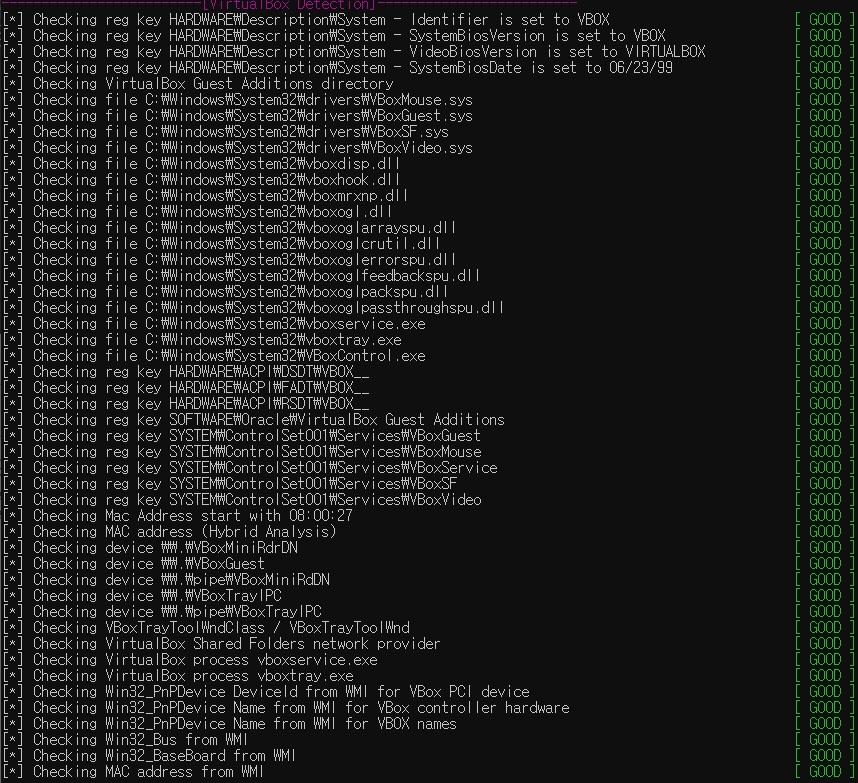

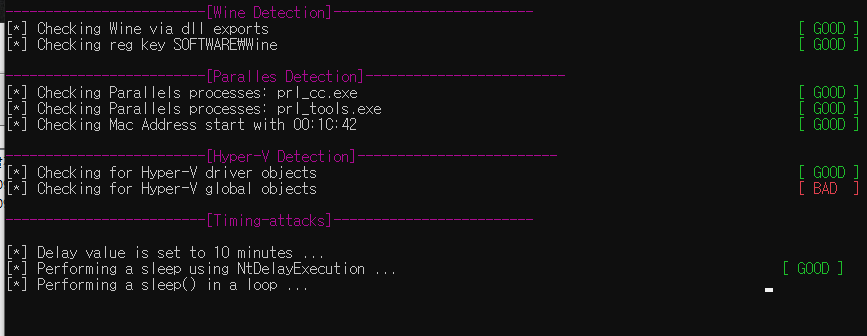
🔹 결론
모든 진행이 완료된 후 BAD 항목에 대한 수정을 진행하여 Anti-VM 악성코드 분석 환경을 개선시킬수 있다.
반응형
'IT Tools' 카테고리의 다른 글
| 사람 찾기 사이트 TruePeopleSearch (0) | 2024.09.22 |
|---|---|
| bitwarden 비밀번호 관리 및 보안 오픈소스 (0) | 2024.09.22 |
| nmap NSE Script_CriminalIP 사용법 (1) | 2024.09.22 |
| Criminal IP란 무엇인가 (1) | 2024.08.29 |
| 스캐닝 툴 recon ng 사용법 (0) | 2024.08.29 |


